Consider the Tacacs Based Product and Continue Looking for Other Products Based on Tacacs
TACACS/TACACS+
- TACACS (Terminal Access Controller Access Control System) is a security protocol that provides centralized validation of users who are attempting to gain access to a router or NAS.
- TACACS+ provides separate authentication, authorization and accounting services.
- TACACS+ uses TCP as transmission protocol therefore does not have to implement transmission control. It uses TCP port number 49.
- If the device and ACS server is using TACACS+ then all the AAA packets exchanged between them are encrypted.
- It separates AAA into distinct elements i.e authentication, authorisation and accounting are separated.
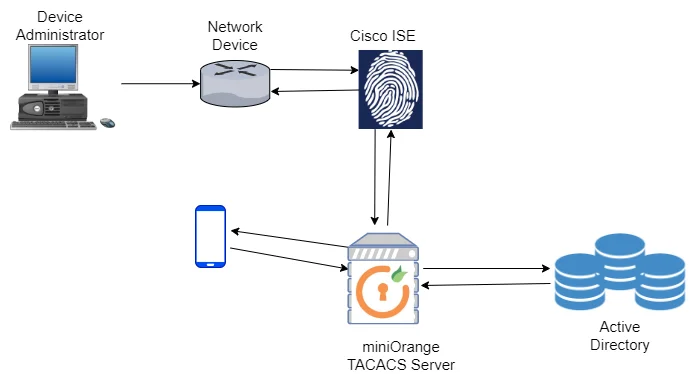
miniOrange TACACS/TACACS+ Authentication
TACACS+ is basically a remote authentication protocol, that will allow a remote access server to communicate with an authentication server in order to validate an user access onto the networking devices. To pass a query to a TACACS+ authentication server, TACACS+ will allow a client to accept a username and password. miniOrange accomplishes TACACS/TACACS+ Authentication by acting as a TACACS Server which accepts the username and password of the user entered on the network device as a TACACS request, validates the user against the user store as Active Directory (AD), prompts the user for the two-factor authentication and either grants/revokes access based on the input by the user.
You can use TACACS+ Vendor-Specific Attributes (VSAs) to manage administrator authorization. TACACS+ VSAs enable you to quickly change the roles, access domains, and user groups of administrators through your directory instead of reconfiguring settings on the firewall.
How does 2FA protect network devices?
Open Wifi Networks: 2FA protects against attempts to steal or phish your username and password via an open wifi network.
Man-in-the-Middle attacks: 2FA doesn't allow hackers to spoof push notifications to your personal device even if your password is compromised by a man-in-the-middle attack.
How to use miniOrange with Cisco TACACS?
- Cisco Access Control System (ACS) is a policy-based security server that provides standards-compliant Authentication, Authorization, and Accounting (AAA) services to your network. ACS facilitates the administrative management of Cisco and non-Cisco devices and applications.
- Cisco Identity Services Engine (ISE) is a security policy management platform that provides secure access to network resources. Cisco ISE functions as a policy decision point and enables enterprises to ensure compliance, enhance infrastructure security, and streamline service operations. Cisco ISE allows enterprises to gather real-time contextual information from networks, users, and devices.
- miniOrange can act as a External RADIUS Identity Store for ACS/ISE. Identity stores that reside outside of ACS and ISE are called external identity stores. ACS and ISE requires configuration information to connect to these external identity stores to perform authentication and obtain user information. Cisco ACS and ISE supports the following external identity stores: LDAP, Microsoft AD, RADIUS Identity Stores.
- miniOrange Push (miniOrange Authenticator App)
- miniOrange Soft Token (miniOrange Authenticator App)
- Google Authenticator
- OTP Over SMS/EMAIL
- Hardware Token (Yubikey, Display Token, etc.)
-
Client - The client is any device, (often a Network Access Server) that provides access services.
-
Server - The server receives TACACS+ protocol requests, and replies according to its business model.
-
TACACS/TACACS+ Authentication - TACACS Authentication is the action of determining who a user (or entity) is. Authentication can take many forms. Traditional authentication utilizes a name and a fixed password. However, fixed passwords have limitations, mainly in the area of security. Many modern authentication mechanisms utilize "one-time" passwords or challenge-response query. TACACS+ is designed to support all of these, and be powerful enough to handle any future mechanisms. Authentication generally takes place when the user first logs in to a machine or requests a service of it.
-
TACACS/TACACS+ Authorization - Authorization is the action of determining what a user is allowed to do. Generally authentication precedes authorization, but again, this is not required. An authorization request may indicate that the user is not authenticated (we don't know who they are). TACACS+ authorization does not merely provide yes or no answers, but it may also customize the service for the particular user. The TACACS+ server might respond to these requests by allowing the service, but placing a time restriction on the login shell, or by requiring IP access lists on the PPP connection.
-
TACACS/TACACS+ Accounting - Accounting is typically the third action after authentication and authorization. But again, neither authentication nor authorization is required. Accounting is the action of recording what a user is doing, and/or has done. TACACS+ Accounting can serve two purposes: It may be used as an auditing tool for security services. It may also be used to account for services used, such as in a billing environment.
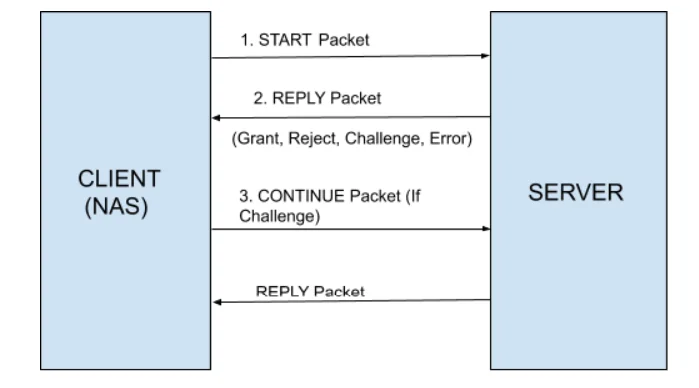
- 1. START
- 2. REPLY
- 3. CONTINUE
-
At first the client sends the START packet to the TACACS server. Every packet sent either way consists of 12 byte Packet header followed by distinguished packet body.The START body packet consists of different fields such as Action, privilege level, authentication type, port, user, remote address and data.
-
The server responds with the REPLY packet. The packet either consist of a request for more information (GETDATA, GETUSER or GETPASS) or a termination (PASS or FAIL).When the REPLY status equals TAC_PLUS_AUTHEN_STATUS_GETDATA, TAC_PLUS_AUTHEN_STATUS_GETUSER or TAC_PLUS_AUTHEN_STATUS_GETPASS, then authentication continues and the SHOULD provide server_msg content for the client to prompt the user for more information.
-
The client MUST then return a CONTINUE packet containing the requested information in the user_msg field. All three cause the same action to be performed, but the use of TAC_PLUS_AUTHEN_STATUS_GETUSER, indicates to the client that the user response will be interpreted as a username, and for TAC_PLUS_AUTHEN_STATUS_GETPASS, that the user response represents will be interpreted as a password.
-
After accepting all the required information server authenticates the client with the same REPLY packet.
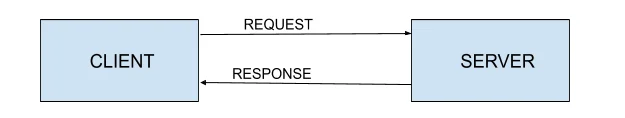
- 1. REQUEST
- 2. RESPONSE
-
TACACS+ protocol provides an extensible way of providing remote authorization services. An authorization session is defined as a single pair of messages, a REQUEST followed by a RESPONSE.
-
The authorization REQUEST message contains a fixed set of fields that indicate how the user was authenticated or processed and a variable set of arguments that describe the services and options for which authorization is requested.
-
The RESPONSE contains a variable set of response arguments (attribute-value pairs) that can restrict or modify the clients actions.
-
The arguments in both a REQUEST and a RESPONSE can be specified as either mandatory or optional. An optional argument is one that may or may not be used, modified or even understood by the recipient.
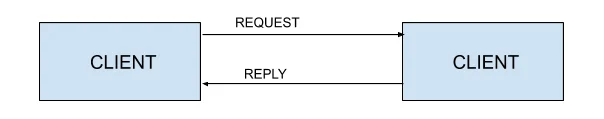
- 1. REQUEST
- 2. REPLY
-
TACACS+ accounting is very similar to authorization. The packet format is also similar. There is a fixed portion and an extensible portion. The extensible portion uses all the same attribute-value pairs that authorization uses, and adds several more.
-
The extra field that the request packet body contain is the 'flags' field which may consist of START(0x02), STOP(0x04) or WATCHDOG(0x08) value.
-
The response to an accounting message is used to indicate that the accounting function on the server has been completed. The server will reply with success only when the record has been committed to the required level of security, relieving the burden on the client from ensuring any better form of accounting is required.
miniOrange supports following Authentication Methods as 2FA for network devices-
TACACS/TACACS+ Terminology
Authentication Flow
There are 3 types of packets which are exchanged in tacacs+ authentication flow,they are -
Authorization Flow
There are 2 types of packets which are exchanged in tacacs+ authorization flow,they are -
Accounting Flow
There are 2 types of packets which are exchanged in tacacs+ accounting flow,they are -
Difference between RADIUS and TACACS
| RADIUS | TACACS |
|---|---|
| Combines Authentication and Authorization. | Separates all three elemenst of AAA making it more flixible. |
| Encrypts only the password. | Encrypts the username and password both. |
| Requires each network device to configure authorization information. | Central Management for authorization configuration. |
| No command logging | Full command logging |
| UDP - Connection Less UDP Port - 1812/1813 | TCP - Connection Oriented TCP Port - 49 |
| Generally used for Network Access | Generally used for Administration |
| Supports one Priviledge Mode | Supports 15 Priviledge Mode |
Why Our Customers choose miniOrange Secure Identity Solutions ?
24/7 Support
miniOrange provides 24/7 support for all the Secure Identity Solutions. We ensure high quality support to meet your satisfaction.
Try Now
Affordable Pricing
miniorange provides most affordable Secure Identity Solutions for all type of use cases and offers different packages based on customer's requirement.
Request A Quote
We offer Secure Identity Solutions for Single Sign-On, Two Factor Authentication, Adaptive MFA, Provisioning, and much more. Please contact us at -
+1 978 658 9387 (US) , +91 97178 45846 (India) | info@xecurify.com
ricethentoorglan1985.blogspot.com
Source: https://www.miniorange.com/tacacs-authentication

0 Response to "Consider the Tacacs Based Product and Continue Looking for Other Products Based on Tacacs"
Post a Comment